Security Assertion Markup Language (SAML)
F�retagsplatsen has support to act as a SAML Service Provider for agencies (only for agencies) with their own identity provider. We support Single-Sign-On (SSO) via SAML 2.0 Web Browser SSO Profile and authentication of API-requests (server to server).
In order to use SAML you need to register your agency for SAML usage with F�retagsplatsen. Please contact us and we will help you with the registration. We will request the following information during the registration process.
- Certificate
- A file with your publiv X509 certificate.
- Issuer name identifier
- The value of the Issuer element in a SAML request.
- Idp SSO service url
- The address to your identity service provider.
- Portal Url
- The address where the user shall be redirected on logout.
You need the following URLs to use our SAML Service Provider.
| SSO URL | See the chapter Single-Sign-On (SSO) for addresses to the service |
| Assertion consumer service URL | https://web.foretagsplatsen.se/Account/SamlLogin |
SAML 2.0 Web Browser SSO Profile
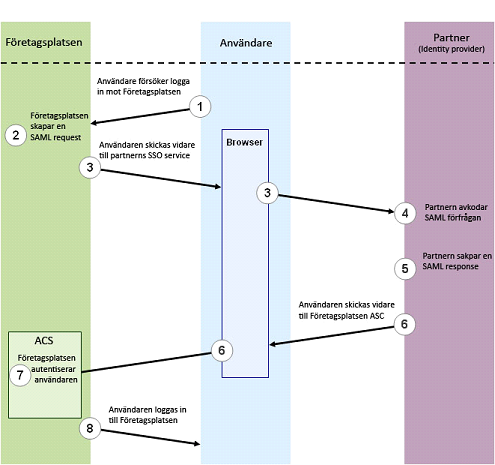
The diagram below shows the flow for Web Browser SSO Profile involving a Service Provider (F�retagsplatsen), an Identity Provider (Partner) and an user with a webbrowser.
- The user tries to login at F�retagsplatsen (see Single-Sign-On for addresses to the service).
- F�retagsplatsen notices that the user is not yet authenticated and creates a SAML authentication request.
- The user is redirected (HTTP-redirect) to the partner's SSO service with the SAML request that was created in step 2.
- Your identity provider decodes teh SAML request and authenticates the user.
- Your identity provider creates a SAML response (SAML assertion) that is being signed with your certificate.
- The user is redirected back to F�retagsplatsen's ASC (Assertion Consumer Service) with teh SAML reponse that was acquired in step 5.
- F�retagsplatsen authenicates the user.
- The user is now logged in and redirected further to F�retagsplatsen's service.
SAML Assertion and temporary users
There are no user details being stored in F�retagsplatsen's system when an agency is using authentication via SAML. Users are created temporarily for each session based on the information in the login-request. Hence, the information that is being sent must be encrypted and contain claims, whose attribute values ends with:
- name
- The user's name
- emailaddress
- The user's email address
- language
- Culture code for which language to use (e.g se-SV for Swedish)
- role
- A list of roles and companies that the user has access to
Below is an example of a SAML assertion.
<AttributeStatement xmlns="urn:oasis:names:tc:SAML:2.0:assertion"> <Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name"> <AttributeValue>test</AttributeValue> </Attribute> <Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"> <AttributeValue>test@pwc.se</AttributeValue> </Attribute> <Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/language"> <AttributeValue>test@pwc.se</AttributeValue> </Attribute> <Attribute Name="http://schemas.microsoft.com/ws/2008/06/identity/claims/role"> <AttributeValue>123456-9876|CompanyLimitedRole </AttributeValue> <AttributeValue>666666-6661|CompanyNormalRole</AttributeValue> </Attribute> </AttributeStatement>
Users and roles
Below are a lists of the different user types and roles
Company users
- CompanyAdminRole
- Company administrator.
- CompanyNormalRole
- Normal company user.
- CompanyLimitedRole
- Limited company user privileges.
Agency users
- AgencyDirector
- Agency administrator.
- AgencyConsultant
- Consultant
SAML API authentication (server to server)
In order for a HTTP request to be authenticated with F�retagsplatsen's API it will need a SamlAssertion field in the header. This field shall contain an encrypted SAML assertion that authenticates the user.
var request = (HttpWebRequest)WebRequest.Create("https://web.foretagsplatsen.se/Api/v2/Controller/Action");
request.Accept = "application/json";
request.Method = "GET";
request.Headers.Add("SamlAssertion", GetEncryptedSamlAssertion());
WebResponse response = request.GetResponse();
using (var reader = new StreamReader(response.GetResponseStream()))
{
string jsonResult = reader.ReadToEnd();
�
}